When the official British history of the First World War revealed that German messages were deciphered, in 1923 the German army realized that a more secure encryption system was required. The Germans eventually obtained approximately 30,000 Enigma machines with slightly more complex designs than were commercially available.
During World War II, the Wehrmacht, Luftwaffe, and German Navy developed individual daily key lists. The beauty of the mechanical encryption system of Enigma machines was that it was very fast and, more importantly, eliminated human error. To create the encrypted text, the unencrypted text was written by the machine, then the encrypted text was formed and transmitted by radio, and the recipient simply wrote the coded message. The machine produced the deciphered text by itself. Moreover, the system was almost unbreakable unless the daily key settings were captured.
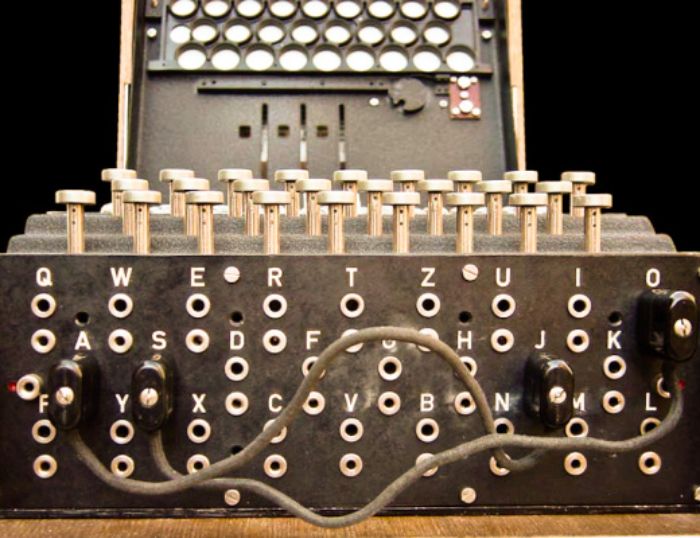
The parts of the Enigma machine

- Reflector
Because this part was not rotating, the encrypted text was automatically sent back onto the rotor discs. As the transcribed text was being typed, the encrypted text was being made automatically at the same time.
- Rotors
Each rotor contained 26 letters of the alphabet and was set to any starting position from A to Z (based on the daily key). In 1938, there were five rotors in the machines. There were 26 contacts on each face of the rotor disc, and they were connected to 26 different contacts on the back. Each rotor was connected differently.
- Plugboard (Stecker)
At first, the Enigma machine could only change six letters before reaching the starting point. However, a wider plugboard developed in 1939 increased this figure to 10.
- Keyboard
The keyboard was for typing the unencrypted text (or receiving the encrypted text).
- Lampboard
They show the encryption of every letter typed by the operator.
The setting of Enigma
The German Army was publishing a new daily key list every month. The book listed the settings that operators should apply every day on all Enigma machines in each Army unit. According to the daily key list, operators rearrange the rotor discs every morning by adjusting their orientation and also changing the plugboard settings. Due to the combination of these systems, a total of 10 billion calculations had to be made to solve one encryption.
To increase the level of security during World War II, the Enigma operator sent a “first message” using the daily key settings, replacing the new setting for the rotors. They were doing it repeatedly to ensure stability. If the daily key requires B-M-Q, a randomly selected three-letter combination could precede the second signal, such as S-T-P-S-T-P, and the receiver had to adjust the rotors accordingly.
How does the Enigma machine work?

To create encrypted text, the unencrypted text had to be typed on the machine. The text created was transmitted by radio, and the recipient was only typing the coded message. The machine was deciphering the text by itself.
- The operator types the unencrypted text. The text is transmitted through the machine by an electric current.
- Letters activated on the plugboard are first encrypted here. They later go directly to the first rotor.
- The following letters pass through the disc and go to a different contact point on the next rotor disc. Also, the first rotor makes a one-letter turn with each letter typed.
- The same process is repeated on the second disc, and as soon as the first disc revolves around the 26-letter cycle, the second disc also makes a one-letter turn.
- The same process is repeated on the third disc, and as soon as the second disc revolves around the 26-letter cycle, the third disc makes a one-letter turn.
- Now each letter reaches the reflector, and the reflector sends it back with discs through a different path.
- The letter moves back from the plugboard to the lampboard. The final encryption is displayed to the operator here.
How was the Enigma code broken?
So, how did Enigma, the strongest encryption device of World War II, get cracked? Due to the fact that it was used by the German Army, the Enigma Machine was seen as a system that could not be broken by anyone. Although some variants of the commercially bought machine were in the hands of Germany’s former enemies, the operation of the military version and the key lists were unknown.
In 1931, however, the French Secret Service bought copies of the machine’s designs and daily key lists from Hans-Thilo Schmidt, a dissident German war veteran. Schmidt continued to provide daily keys over the next few years. But the French made little use of them. Poland opened the door.
Aware of Germany’s ambitions for its territory in the 1930s, the Polish cipher bureau, Biuro Szyfrow, made it a priority to crack the Enigma machine. Through an agreement with France, most of the materials related to Enigma were transferred to the Poles, and they began to make copies of the machine. Poles realized that the Enigma machine’s mechanical system could only be studied with mathematics, not linguistics. It was a stimulating idea. In the later years, many mathematicians who were familiar with the German language emerged from the Polish lands, which were previously occupied by Germany. Among them was Marian Rejewski.

- Message key
Rejewski focused on the Enigma’s “start message” key, consisting of three letters sent at the beginning of each message. As there were only three rotors, he realized that every fourth letter should correspond to a different encrypted form of the first letter, so he found a crack in Enigma’s armor.
There was still no idea of the daily key, but he began to search for substitution links or chains. When he had access to a sufficient number of messages per day, he managed to draw a table for the relationships between the first and fourth, second and fifth, and third and sixth letters in the message key.
- Chains
By examining these tables, he determined the chains, that is, how many links there were before the first letter was attached to itself; in this case, there were three links, A-U, U-S, and S-A. Rejewski realized that the plugboard settings could not be determined, but the number of links in each chain was a reflection of the rotor settings. Some chains were long, some were short.
Rejewski and his colleagues spent a year drawing out the tables for each of the 105,456 possible rotor settings, establishing a relationship between them and the lengths of possible chains. Then, when the Germans changed their protocols and made these tables useless, Rejewski developed electronic calculating machines called “bombe” to rearrange the tables.
- Plugboard
Rotor settings were resolved with tables, but plugboard settings were not resolved yet. When Rejewski and his colleagues thought they’d figured out everything by using the rotor settings table, something else piqued their interest: Sometimes, some messages were understandable:
CANVAYS EN RAUTE
They realized that some letters might have been switched on the key table. So in the case of “a” and “o”, the encrypted message above translates as follows:
CONVOYS EN ROUTE
England receives the Enigma plans
Rejewski’s finding enabled Poland to read Enigma signals for much of the 1930s. However, with the introduction of two additional rotors and a larger plugboard in 1938, the Enigma machine again posed a new difficulty. Just a month before Germany invaded Poland in September 1939, the Poles managed to deliver a copy of the Enigma machine, their “bombe” plans, and Rejewski’s analysis to England.
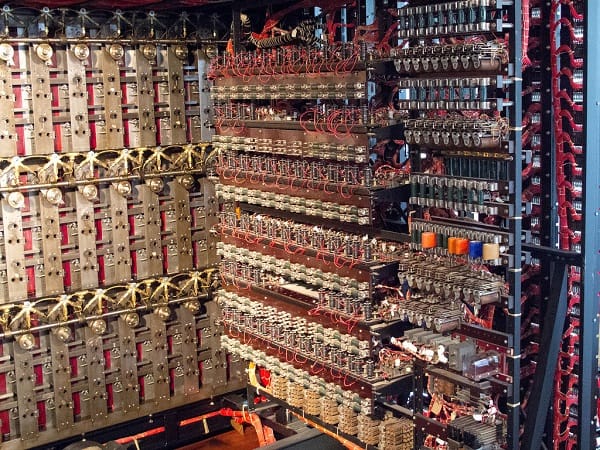
Alan Turing at Bletchley Park
Alan Turing, a young and talented mathematician from Cambridge, was among the diverse employees of the new British decoding center in Bletchley Park. Before joining the center, Turing was working on duality in mathematics and programmable computers. Seeing the success of Poland, Turing set out to design a series of more advanced “bombes” to crack the new rotor settings of the Enigma machine.
It was necessary to work swiftly, as the settings of the Enigma machine changed every midnight. If it were not for some clues that were spotted before Turing arrived at Bletchley Park in 1939, the number of settings would probably be too much to work on.
Jumbo and Colossus
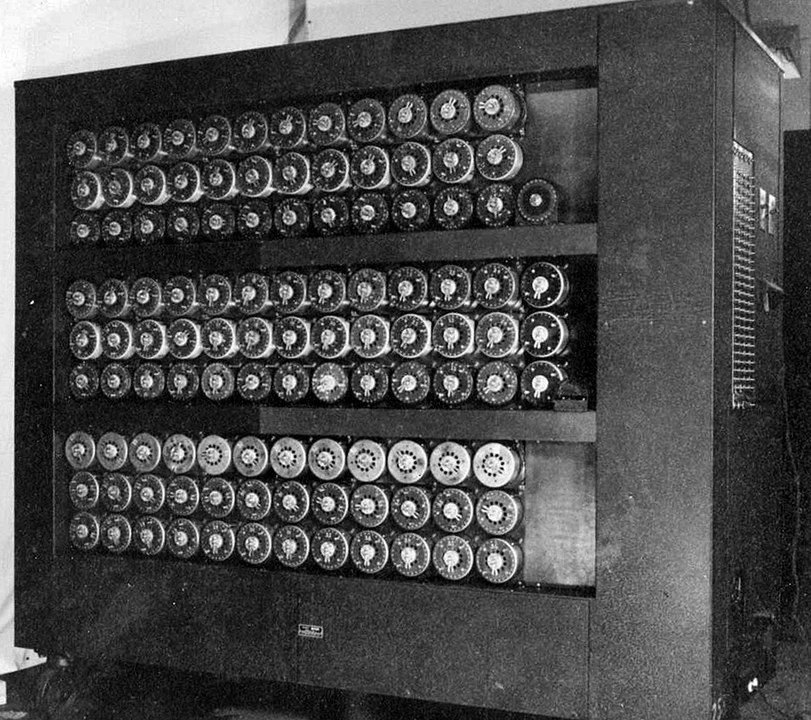
Alan Turing’s plan to develop sequences, interconnected “bombes” arranged to reveal cycles, was approved, and he was allocated 100,000 pounds to create them. Each bombe consisted of 12 sets of rotor copies, the first of which was called “Victory,” which began operating in March 1940. As the prototype continued to be tested and developed, the Germans changed the message key protocols, which caused a serious interruption in the decryption.
However, an improved bombe began to be used in August, and by the spring of 1942, 15 more came into use. The “Cribs”–bombs operating through rotor settings and message keys—were operating at great speed. On a good day, the system could unravel all this in one hour, decoding other signals for the rest of the day.
By the end of the war, more than 200 bombes were in use. However, this whole process was based on finding the right “cribs,” so the locomotive of the system was still human ingenuity.
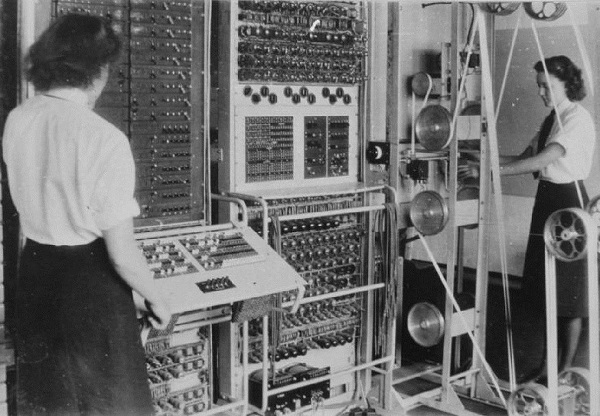
Eventually, the number of bombes and the connections between them created the world’s first programmable computer. The name used by the operators for this computer with the code name “Jumbo” was “Heath Robinson.” In 1942, Turing found a shortcut to decrypt Lorenz, an adapted version of the Enigma machine Geheimschreiber that is used by the German Navy. He explained his ideas to Tommy Flowers and Max Newman, and they created a computer named Colossus. Colossus, a more integrated, programmable digital device, was the real ancestor of the modern computer.
In July 1942, Turing traveled to America to share his ideas with US decoders. Although the British shared their secrets with their Western allies, and Bletchley Park also struggled to decipher the Italian and Japanese ciphers, the answer to the question “How did Enigma get broken?” remained a secret until the 1970s.
The steps by which the Enigma machine was cracked
- Cillies
Some Enigma operators didn’t use completely random message key combinations because they made mistakes or were too lazy to try new ones. When these were found, they gave the decoders useful clues. This made it possible to keep an eye on the signals from those operators.
- Rotor codes
The Germans assumed that making sure that no rotor disc was in the same place for two consecutive days made the system safer. On the contrary, it was a weakness because, when the position of one or two rotor discs was determined, the number of possible remaining combinations was greatly decreased. Also, it was easier to detect the possible combinations for the next day.

- Cribs
Identifying the known words in a message, “cribs,” could help in finding the settings. Some types of signals were predictable and based on a specific formula. For example, the signals of weather stations usually start with or contain the German word “Wetter.” These kinds of signals were carefully observed and identified with good predictions. Another “crib” was to place mines in a particular area and try to trace their geographical coordinates in German submarine messages.
- Pinch
Obtaining the German key lists was one of the priorities. During the Atlantic War, both German submarines and airships were raided; key lists were captured and vehicles were sunk so that the Germans were not aware of the losses.
- Loops
Turing was also working on the question of what would happen if the Germans stopped repeating the message key. For this purpose, he focused on deciphering archives and began to identify “loops” that were not so different from Rejewski’s “chains.” When a text was known or “crib” was predicted, the loops made it possible to reveal the rotor settings. Thus, Turing discovered another shortcut.
- A lot of machines
Turing thought he would have the chance to review 17,576 different possible settings in a short time if he arranged a sufficient number of bombes to run sequentially, each imitating the action of another rotor disc. But he still needed a mechanical shortcut. He accomplished this by connecting successive machines and building circuits between them. In this way, the existence of a loop was shown by a light bulb in the circuit.
- Plugboard
Just like Rejewski, Turing put the plugboard problem aside and minimized it. Because with a correct crib, it was possible to obtain a deciphered word containing strange letters, and when these letters were replaced correctly, the settings of the plugboard were revealed.
Bibliography:
- Winterbotham, F. W. (2000) [1974], The Ultra secret: the inside story of Operation Ultra, Bletchley Park and Enigma, London: Orion Books Ltd, ISBN 978-0-7528-3751-2, OCLC 222735270
- Gaj, Kris; Orlowski, Arkadiusz (May 2003), “Facts and Myths of Enigma: Breaking Stereotypes”, in Biham, Eli (ed.), Advances in Cryptology — EUROCRYPT 2003: International Conference on the Theory and Applications of Cryptographic Techniques, Warsaw, Poland: Springer-Verlag, pp. 106–122, ISBN 3-540-14039-5, LNCS 2656
- Gannon, James (2002), Stealing Secrets, Telling Lies: How Spies and Codebreakers Helped Shape the Twentieth Century, Washington, D.C.: Brassey’s, ISBN 978-1-57488-367-1